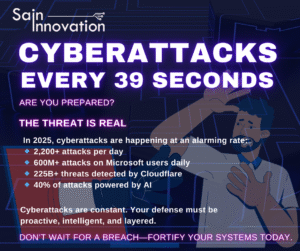
World wide in 2025, there are an estimated 2,200 cyber attacks per day. This translates to a cyber attack occurring approximately every 39 seconds. These attacks range from ransomware to phishing and social engineering attempts, and they are increasingly powered by artificial intelligence.
In the first quarter of 2025, there were a record-breaking 2,063 ransomware victims according to ZeroThreat, with a significant increase in ransomware attacks listed on data leak sites.
A growing number of modern cyber incidents are no longer just the result of traditional hacking techniques but are increasingly being driven by Artificial Intelligence (AI). Research and industry reports suggest that around 40% of cyberattacks today are AI-powered or AI-assisted. This means attackers are leveraging AI to automate phishing campaigns, create highly convincing deepfakes, develop self-learning malware, bypass security controls, and even identify system vulnerabilities faster than human hackers.
Unlike conventional attacks, AI-powered threats can adapt in real time, scale rapidly, and mimic human behaviour, making them harder to detect. For example, AI can generate personalized spear-phishing emails by analyzing social media and communication patterns, or it can deploy bots that continuously evolve to avoid detection.
This shift highlights a new era of cybersecurity where defenders must also rely on AI-driven security tools and machine learning models to detect anomalies, predict attack patterns, and respond proactively. Organizations that fail to adopt AI in their defense mechanisms risk falling behind, as attackers are already weaponizing it at scale.

The education and research sector continues to experience the highest volume of cyberattacks, making it the most targeted industry. The manufacturing sector is a primary victim of ransomware campaigns, while the government and telecommunications sectors have also witnessed a sharp rise in attacks, according to Check Point research.
Overall, these trends highlight that the entire digital ecosystem is under constant threat, with no industry left untouched by cyberattacks.
In Q1 2025 alone, 12,333 new vulnerabilities were reported globally, reflecting the rapidly growing attack surface across applications, operating systems, and enterprise technologies. What makes this trend more alarming is the 75% surge in actively exploited flaws, meaning cybercriminals are not just discovering weaknesses—they are weaponizing them at an unprecedented pace.
These vulnerabilities range from zero-day exploits in widely used software to misconfigurations in cloud platforms and IoT devices. Attackers are increasingly automating vulnerability scanning and exploitation using AI-driven tools, allowing them to compromise systems within hours of disclosure.
For organizations, this highlights the urgent need for proactive vulnerability management, including regular patching, threat intelligence integration, and continuous monitoring. Without swift action, even a single unpatched flaw can serve as a gateway to large-scale data breaches, ransomware infections, or supply chain attacks.
Business Email Compromise (BEC) continues to rank among the most damaging cyber threats facing organizations worldwide. In these attacks, fraudsters employ highly sophisticated social engineering tactics to impersonate executives, employees, or trusted partners within the organization. Unlike mass phishing, BEC campaigns are highly targeted and personalized, often involving in-depth research on company hierarchies, vendor relationships, and communication styles.
Attackers use these insights to craft convincing emails that mimic legitimate internal communications—such as urgent payment requests, invoice modifications, or sensitive data transfers. Modern BEC schemes are also leveraging AI tools to refine language, remove grammatical errors, and even generate real-time responses, making them increasingly difficult to detect.
The financial impact of BEC is staggering, with global losses measured in billions of dollars annually. Beyond financial fraud, these attacks erode trust, damage reputations, and expose organizations to regulatory risks.
Defenses against BEC require a multi-layered strategy—including strong email authentication protocols (SPF, DKIM, DMARC), continuous employee awareness training, AI-powered anomaly detection, and strict internal verification processes for financial or sensitive requests.
Ransomware continues to show a strong regional concentration, with 59% of all victims located in the United States. This dominance can be attributed to several factors:
Economic strength and digital dependence: The U.S. has a large number of enterprises and critical infrastructure sectors that heavily rely on digital systems, making them lucrative targets.
High ransom-paying potential: Attackers perceive U.S. organizations as more likely to pay higher ransoms due to stronger financial capacity and operational urgency.
Regulatory and reporting mandates: Stricter breach disclosure laws in the U.S. contribute to higher visibility of attacks compared to other regions, where incidents may go unreported.
Targeted sectors: Healthcare, education, finance, and government agencies in the U.S. are frequent ransomware targets due to the sensitive and mission-critical data they handle.
This regional skew highlights how cybercriminals strategically direct their campaigns where the return on investment (ROI) is highest, while also suggesting that geopolitical and economic landscapes influence ransomware operations.
1. User Awareness & Training
Over 90% of cyber incidents stem from human error, such as phishing or weak passwords
Regular training—like phishing simulations and awareness programs—helps reduce risk
2. Passwords & Multi-Factor Authentication (MFA)
Use strong, unique passwords. Avoid reuse across accounts.
MFA is highly effective: one stat shows 99.9% of account-compromise attacks can be prevented by enabling MFA.
3. Patch Management & System Hardening
Keep all software, OS, and applications up to date. Automated patching is key.
Disable unnecessary services like RDP or PowerShell unless needed—if enabled, protect with strong credentials and logging.
4. Secure Configurations & Least Privilege
Limit administrative access to only those who need it; use non-privileged accounts for everyday tasks.
5. Web Filtering & Email Security
Filter out malicious websites and email attachments.
Since phishing is a dominant attack vector (over 90% of incidents start with phishing) email-level defenses and user education are essential.
6. Backups
Maintain regular, secure backups. Restoring from backups is often safer than paying ransom and can reduce downtime.
7. Proactive Tools & Zero-Trust Models
Employ SIEM (Security Information and Event Management) and AI-driven analytics for real-time threat detection and response.
Consider a zero-trust model—verify every request regardless of origin
Proactive cybersecurity strategies (e.g., threat intelligence, automated scanning) are becoming increasingly necessary
8. Incident Response Planning
Prepare in advance for breaches: pre-designate an incident response team, define roles, and have procedures in place
Frequency: Cyberattacks are continuous—ranging from hundreds per second to billions per day, depending on measurement scope.
Defense: A combination of awareness, strong authentication, updated systems, correct configurations, proactive detection, and solid response plans is your best defense.